Combat software, or specialized military software, started developing rapidly in Ukraine due to the urgent needs of the battlefield. Recently, Ukrainian legislation officially classified specialized software and other defense-related IT solutions as weapons and military equipment.
These systems enable the collection, processing, use, and dissemination of data, as well as the transmission of information about objects and events in the operational environment. They support horizontal and vertical information exchange, ensure coordination of friendly forces and assets, provide firepower advantages, and enable real-time command and control processes at all levels and across all domains and dimensions of warfare.
In May 2025, Ukrainian security expert Kateryna Aniskina published a report — the first of its kind to explore the issue of specialized software in the context of its practical use by the Ukrainian Armed Forces in the ongoing Russian-Ukrainian war. The report is available in Ukrainian; an English translation is forthcoming.
I’ve summarized the key findings from this research paper and am sharing them here for public access.
-
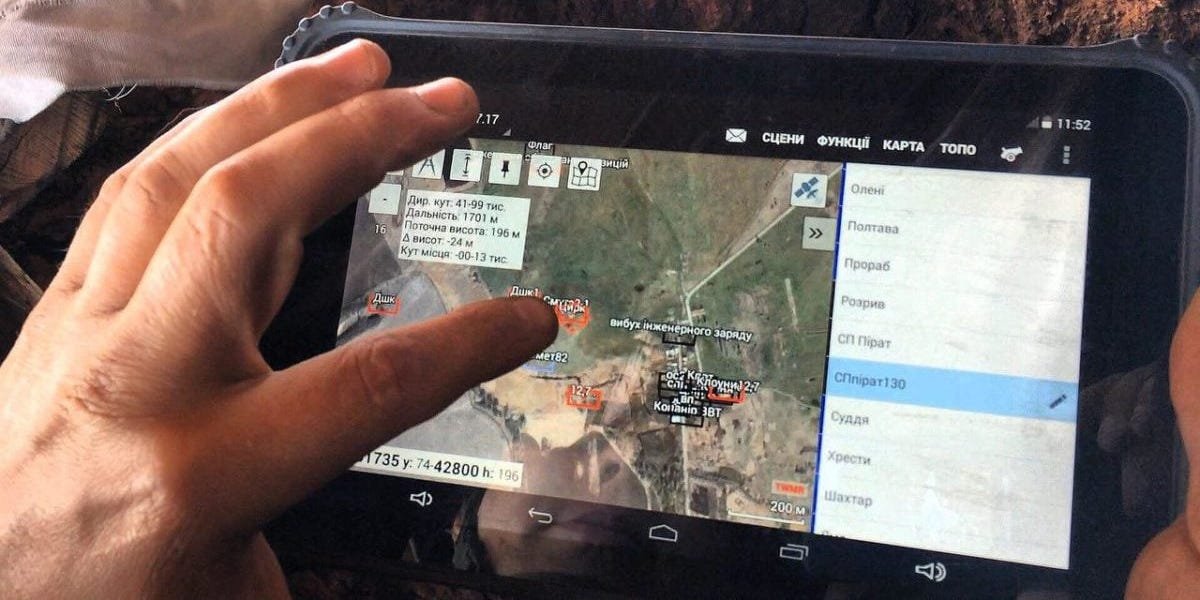
In the Ukrainian context, situational awareness systems have seen the highest demand at the tactical level. This phenomenon can be explained by the fact that approximately 90% of the army is concentrated at that level.
-
According to a survey conducted by the Ministry of Defense of Ukraine via the “Army+” app, with around 10,000 service members participating, the systems “DELTA,” “Virazh-Tablet,” and “Kropyva” were identified as the most frequently used by the military.
-
At the operational level, a so-called “gentle Deltanization” (from the name of the DELTA system) is underway, while at the tactical level, there are observable attempts by other systems and teams to “integrate with Kropyva.” In other words, current standardization at the tactical level is not based on any clearly defined standard, but everyone acknowledges that Kropyva is universally present, and blindly tries to adapt to that fact.
DELTA
-
Over the past few years, DELTA, which was officially commissioned in August 2024, has evolved from a situational awareness system (its originally intended function in the form of a digital map) into an ecosystem of interconnected products, which now also includes elements of command and control.
-
This ecosystem brings together several modules and tools, including:
-
Monitor – a situational awareness module built to NATO standards (also available as the mobile app Monitor Mobile);
-
Vezha – a module for operational interaction, decryption of UAV video streams, and flight statistics (this absorbed the Tube module, which previously functioned as a streaming tool for unmanned systems and stationary cameras);
-
Mission Control – a synchronization matrix for planning flight missions;
-
Element – a secure chat platform (also available as a mobile app);
-
Target Hub – a module for target data integration;
-
Nextcloud – a cloud storage solution similar to Google Drive.
-
-
According to the developers’ overarching concept, all components of the ecosystem are designed to function in coordination with one another.
-
A distinctive feature of DELTA is its interoperability with a number of IT systems used by NATO member states, which—when needed—enables real-time data exchange with partner forces.
-
According to NATO authorities, Delta has achieved increased interoperability with NATO systems as its multidomain situational awareness toolset is based on NATO standards and specifications. “While Delta has not been adopted/adapted by NATO, it could potentially be used for planning joint military operations of different scales and complexity,” Janes reported. In April 2025, one NATO state was in talks with Ukraine to acquire DELTA.
-
The data processed by the system can include real-time inputs from UAVs, as well as text files, satellite imagery, radar data, and other sources, including data received from other systems.
-
The system is used most extensively at the tactical and operational levels. Currently, DELTA has tens of thousands of users.
-
Unlike narrowly specialized solutions, DELTA is a broad system that, with few exceptions, spans nearly all branches and types of military forces and units, though it does not have a clearly defined specialization.
-
Does DELTA currently offer a complete set of tools that fully meet the needs of all service branches? Not yet—but the foundation is in place for all of them.
-
The system’s tools enable the following chain of interaction: ISTAR units collect all available raw data from all accessible sources (informant reports, automated sources such as chatbots and other information systems, satellite imagery, aerial reconnaissance data, radar, cyber data, etc.) → then, various actors within the security and defense sector input this information into DELTA, layering it onto the digital map. The system’s tools then convert this data into a standardized, machine-readable format, eliminating any room for interpretation. For example, an object on the map—such as a piece of weaponry or military equipment (WME)—is precisely the object entered into the system and cannot be interpreted otherwise. → The processed information is objectively displayed on the digital map in near real-time and becomes accessible to other actors who require situational awareness on the battlefield.
-
DELTA is integrated with numerous specialized software systems, including Virazh, Kropyva, Hrafit, and the American ATAK system.
-
Among other updates, it is worth mentioning the team’s efforts to implement the MDM (Mobile Device Management) approach. MDM essentially creates a secure environment on a military user’s device, serving as an additional security layer by granting access to a catalog of restricted military applications. Only the “military” environment of the user is controlled, while their personal environment remains inaccessible. Notably, in the event of device loss, an administrator can remotely trigger the deletion of all data related to the military secure container.
-
A high level of DELTA security is ensured by several factors, including:
a) deployment in a cloud environment;
b) the use of FIDO2 — a physical security key (cryptographic token) for multi-factor authentication, considered resilient to phishing attacks due to asymmetric cryptography;
c) the presence of a dedicated verification and support service;
d) an internal security team (SOC, Security Operations Center), which includes software protection and human-factor checks;
e) regular penetration testing (PENTEST) conducted by allied partners, enabling the identification of critical vulnerabilities in the integrated command system during testing.(I wrote about DELTA in one of my recent newsletters here).
Virazh and SkyMap
-
Among the systems supporting air defense are the specialized software solutions Virazh-Tablet (hereafter, Virazh), SkyMap, and the automated control system Krechet.
-
Currently, there are two branches of air defense: the Air Defense of the Air Force and the Air Defense of the Ground Forces. Virazh operates in support of the Air Force, while SkyMap is used in support of the Ground Forces of the AFU.
-
The Virazh system consists of functionally integrated hardware and software tools and represents a “conglomerate” of about 50 different programs (applications) that can communicate with each other.
-
For instance, Virazh-ZRV is considered one of the core elements of the Virazh system — this system automates the collection, analysis, display, and exchange of information about the air situation.
Virazh-RD is a system for operational-tactical calculations and combat simulation modeling, classified as a training and simulation complex. It allows users to conduct training under dynamically changing air situation conditions; practice coordination and support of combat operations across all branches of the Air Force. -
According to an industry expert, today, the majority of air defense military personnel in the Air Force of the AFU use Virazh for their work, with tens of thousands of users.
-
As of now, this system is not codified, and the Virazh team itself is very small—especially relative to the number of users and the system’s demand—and is experiencing resource shortages.
-
Another system, SkyMap, is a real-time automatic coordinate streaming system deployed along the entire frontline, at every operational tactical unit, with several active instances within the country.
-
It is a decentralized solution (like both the Virazh and Krechet systems), meaning that each operational tactical headquarters has its own SkyMap.
-
Both systems operate over VPN (which provides one level of encryption) plus an additional encryption layer, making these systems very difficult to hack. These systems effectively ensure an adequate level of security despite not being codified. In other words, it can be said that technology currently outpaces legislation.
Kropyva and ARMOR
-
Kropyva is often called the “standard software that everyone has.”
-
It is the system most deeply and widely integrated into the troops. As of today, its user base numbers in the hundreds of thousands.
-
Originally, Kropyva was designed for artillery use as a ballistic calculator. However, over time, it has “grown” with a large number of new features, though it has not reached the operational level, remaining deeply integrated at the tactical level where command functions are absent.
-
Kropyva allows users to mark objects on an offline map, and simple communication is also possible: for example, data from Vezha (or DELTA) can be “uploaded” to Kropyva. Data exchange occurs directly and quickly but not with neighboring battalions (meaning data transmission is segmented).
-
Among similar systems is also ARMOR. Today, ARMOR is a tactical-level system that provides firing calculations from covered firing positions for tanks, infantry fighting vehicles (IFVs), armored personnel carriers (APCs), tube artillery, mortars, multiple rocket launchers (MRLs), anti-aircraft artillery, and group infantry weapons.
-
The system was developed for artillery, mechanized units, and air defense units, which, thanks to its use, can fire from covered firing positions, enhancing their safety while limiting the enemy’s ability to conduct counterfire. In addition, the system provides high accuracy in target engagement across all firing range bands, even if targets are concealed by natural barriers, vegetation, or terrain. Today, there is no brigade without ARMOR in use.
-
The system is implemented as a mobile application, the primary purpose of which is to calculate target engagement parameters from covered firing positions for a wide range of weapons (which can be considered its core function).
-
The system covers over 60 different weapon types and more than 100 types of ammunition. Here is how it works: the software is installed on a tablet and can be used together with existing fire weapons. “The user simply needs to determine their own position [the firing weapon’s position], select the weapon from the available list, orient it on the terrain, set firing conditions, identify the target, and receive target engagement parameters for the chosen weapon,” the developers explain. After that, the weapon is aimed according to the calculated parameters and fired.
-
ARMOR enables more precise, faster, and safer target engagement with significant ammunition savings. Here, “precision” means the ability to calculate so that the target can be hit within 1–3 shots. Regarding speed, it refers to rapid receipt of meteorological data for gun adjustments and faster weapon orientation compared to typical methods.
-
Overall, the time to engage a target is reduced from approximately 30 minutes to 5–7 minutes using the application. Safety is achieved by reducing the time spent in enemy return-fire zones, avoiding direct exposure zones, minimizing engagement time, and reducing the number of personnel involved. Ammunition savings are achieved by significantly decreasing ammunition expenditure (by 5–10 times), which also extends the service life of the weapons.
-
It is worth noting that although ARMOR and Kropyva are designed to solve similar problems, they do so in different ways. Kropyva has broader functionality, while ARMOR more effectively addresses the core task—precise target engagement.
Current Problems and Challenges of Combat Software in Ukraine
-
Shortage of trained communications specialists in the Armed Forces of Ukraine poses a challenge both for the military and the sector as a whole.
-
The outdated nature of educational institutions and programs.
-
Insufficient (and sometimes almost nonexistent) technological support for command and control units, preventing full utilization of the systems.
-
Need for more systematic financial support from the state. Currently, government funding for such projects is limited to one-time (and relatively small compared to needs) grants awarded through themed hackathons (for example, Brave 1, a state initiative by the Ministry of Digital Transformation). However, these are grants, not systemic funding. The responsibility for attracting external financial resources in the form of one-time grants, donor funds, and/or investments falls on the developers themselves.
-
Investment challenges: Both Ukrainian and foreign investors tend to prefer hardware solutions, because, for instance, a UAV delivers visible, tangible results on the battlefield, even to non-expert audiences.
-
Lack of clearly defined standards for building specialized software. This is a key factor when discussing inter-system interoperability and further sector development. Currently, implementing standards that would require systems to “speak the same language” by supporting uniform standards, formats, and unification is a primary task for improving interoperability.
-
Lack of interoperability forces soldiers to use a large number of systems simultaneously on different devices, creating significant practical inconveniences.
-
The existence of a “software zoo”—a large number of fragmented systems with different purposes. The state lacks control over the data storage sources, which are operated by many dispersed private systems.











